WannaCry: How to avoid it and what to do if you get it
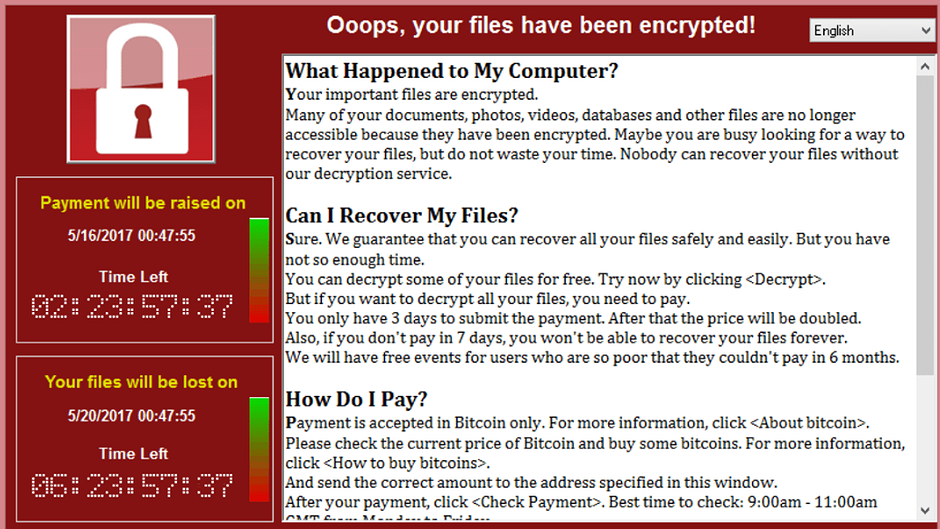
The world’s most widespread cyberattack struck almost 150 countries, including China, Egypt, Jordan, Russia, Turkey, Saudi Arabia, and the UK. The Ransomware dubbed WannaCry began to infect computers on Friday and continued to spread Monday. With over 200,000 computers infected so far, users were asked to pay $300 in bitcoins to regain access to their computers.
The UK’s National Health Service, Spanish telecom giant Telefonica, French carmaker Renault and numerous banks across Europe were among the bigger institutions hit by the Ransomware.
We spoke with two digital security experts, Rory Byrne of Security First and Amin Sabeti of Small Media for their perspectives and advice on the incident:
1. Was this cybercrime attack preventable?
This particular attack was preventable. It occurred because of the leak of a security hole (or exploit) that was found by US intelligence agencies and used to hack into some of their targets. However, when a series of these were recently leaked, it meant that criminal hackers were able to utilise the same flaw to infect users with ransomware.
This is a scenario that many security experts have been warning about for many years. Also, many of the systems that are infected, such as Windows XP, are no longer fully supported by Microsoft, so were left more vulnerable to WannaCry.
We need to keep in mind that this attack was not a sophisticated attack and people could and would protect themselves by keeping their OS up to date. Even without having an anti-virus.
2. Do you advise people to pay a ransomware?
If you have been affected by WannaCry specifically we recommend that you use this guide to remove it. There are a number of tools that are being released that claim to decrypt it, some of which are likely to be fake. We suggest only using those from well known security firms such as Norton, Sophos, Avira, Malwarebytes etc. Also, you can check The No More Ransom Project as one of the solutions to deal with ransomware.
We have been asked to advise on a ransomware cases before where all alternate options were not possible as backups had been affected and no removal software was available. In that case, paying the ransom was the only option for the organisations to recover their data.
One of the problems with WannaCry though, is that it appears it was way more successful than the authors had imagined and there are reports that they have been overwhelmed by people seeking to retrieve the unlock code. As such, there is a high chance that if you do pay the ransom, you may not receive the key or that it may take longer than normal to be able to decrypt your files.
3. How do people protect their devices from these kinds of attacks?
There are a few basic steps that users and organisations can take to prevent or mitigate the effects of ransomware:
- Use officially purchased and supported versions of software and automatically install the latest security updates
- Run an antivirus and firewall
- Ensure you understand phishing emails and do not open suspicious attachments
- Store encrypted backups of your files and keep at least one version physically disconnected from the internet so that they cannot be affected by ransomware.
For more technical users involved in incident response to a ransomware attack, we have contributed to a short checklist available here.
Want to know more about the basics of digital security? Protect your data and your sources by signing up here for Advocacy Assembly’s free courses taught by Security First.
This blog was written by Rory Byrne and Amin Sabeti.
Rory Byrne is the CEO and Co-founder of Security First. Rory has worked at the intersection of technology and human rights, developing digital solutions and providing targeted training for human rights defenders. For more follow Rory on @roryireland
Amin Sabeti is a digital security analyst and trainer, managing digital projects with Small Media. He has led numerous workshops on topics such as cyber security, phishing and malware, training NGOs and international activists. Amin tweets at @AminSabeti in English and Farsi.
Related courses

90 mins
 School of Data
School of Data
90 mins
 School of Data
School of Data Rory Peck Trust
Rory Peck Trust
50 mins
 Rory Peck Trust
Rory Peck Trust
Blogs

6 useful resources for journalists covering Covid-19
With a global pandemic spreading throughout the world, journalists are under increasing pressure to report accurate and relevant news for the masses. Often when covering a crisis, those on the reporting frontlines compromise their physical safety and mental health. To show some solidarity, the Advocacy Assembly team curated a list of useful resources from other organisations leading the way on this.

5 ways to find data for your next story
Data journalism is fast becoming a big trend in newsrooms across the globe. However, data isn’t always so easy to find. Here are five ways to get data for your next article.



